As is often the case with security vulnerabilities they come in pairs, and the better named ones get all the attention. This was very much the case last week with both KRACK and ROCA being made publicly available. The industry attention was very firmly focused on the KRACK-WPA2 wireless attack which enabled attackers to access wireless networks without authorisation. However, much less attention has been focused on the ROCA attack which can enable the decryption of Bitlocker and ChromeOS full disk encryption on certain manufacturer's hardware.
Return Of Coppersmith's Attack (ROCA) is a vulnerability in the way the Trusted Platform Module (TPM) generates RSA key pairs for the purpose of encrypting or signing information. Researchers at a number of Universities across Europe discovered the vulnerability early this year and have been withholding their research for ten months while manufacturers produce fixes for this issue. These fixes have now been released but as the problem is with the embedded TPM chip's firmware the update process may not be simple to deploy remotely.
The main focus of concern for most organisations is the use of the TPM chip in full disk encryption processes, namely Bitlocker. As part of the setup for this system the TPM chip is used to generate public/private key pairs for use in the encryption process. The research found that the version 1.2 TPM chip has not been generating strong key pairs, this has reduced the time required to break the full disk encryption on current hardware from impossible to highly achievable. The National Cyber Security Centre (NCSC) has costed this up using an Amazon instance at $40 for a 1024-bit RSA key and $20,000 for a 2048-bit RSA key.
If you are using Windows Bitlocker you can review the hardware platform you have deployed this on as the vulnerability is in the TPM chip - this will vary depending on manufacturer.
Please note: this will also impact server hardware that is using the TPM chip. This link will take you to a page that provides vendor specific support.
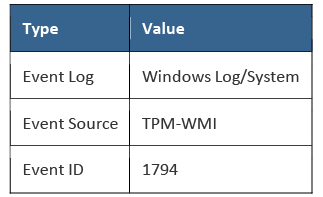
Windows has released an advisory for this issue and an update will be made available that will alert on any device currently running the vulnerable version of the TPM chip and enable organisations to target the firmware update to these devices only. The event log info is below but will require log centralisation to make searching effective.
Windows has also provided a PowerShell script that can be run remotely on each machine in the enterprise to determine if the system is vulnerable. This script can be found on the bottom of this link.
Once you have applied the firmware update you will still need to rotate the RSA keys used to totally mitigate this vulnerability.This won't require a complete decrypt but will require a manual process to force this rotation.
While this vulnerability is serious and could cause a compromise of data please measure your response based upon your likely threat actor. Anyone exploiting this will need physical access to the device, if you are using 2048-bit RSA keys the required computation is still expensive although I would expect this to come down as GPU and ASIC powered systems are used. My recommendation: get the 10th October windows updates deployed, identify your affected assets, prioritise high value systems or users and build a remediation plan. Expect to expedite this if you are using 1024-bit or further information come out about the accelerating the decryption of 2048-bit.
Get in touch
If you want some further guidance on mitigating, or to understand if your organisation is vulnerable to the KRACK or ROCA. please get in touch with your account manager or send us a message using the button below.