In this edition, we will focus on the patches by Microsoft, Adobe, Cisco, Fortinet, SAP, and VMware.
Again, there have been quite a few zero-day exploits identified, with many of these known to have been actively exploited in the wild.
Microsoft
In their November Patch Tuesday release, Microsoft has addressed 58 vulnerabilities; only 3 of those rated as Critical, although there are 5 zero-day vulnerabilities. The patches cover a broad array of applications and services, including Windows (10, 11, and Servers), Visual Studio, Exchange, .Net, Office, SharePoint, Azure, and more. Additionally, there have been 20 Edge/Chromium based vulnerabilities identified.
This month's vulnerabilities chiefly revolve around Elevation of Privilege (EoP), Remote Code Execution (RCE), and Spoofing.
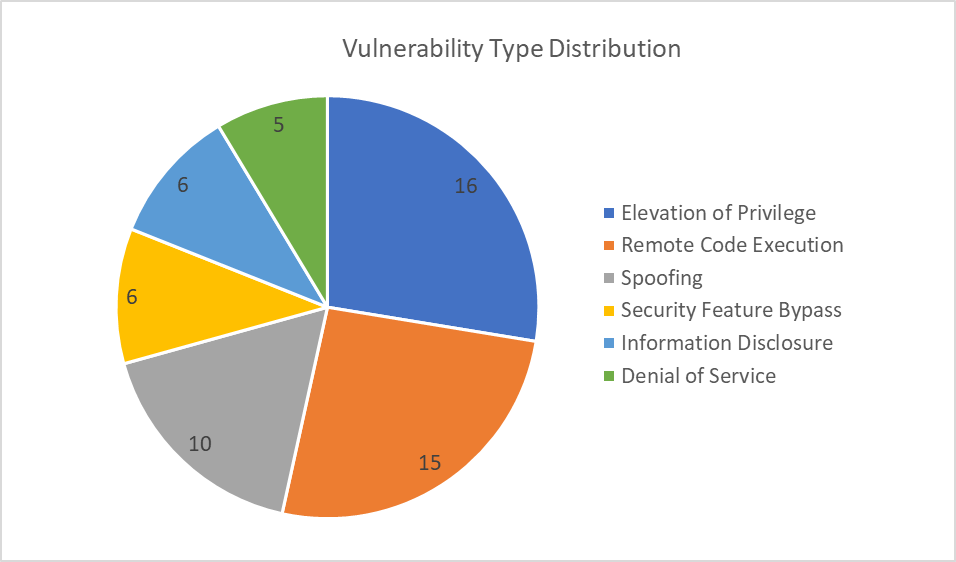
Outlined below are the Actively Exploited and Critical vulnerabilities detailed in this month’s Patch Tuesday:
Actively Exploited in the wild
1. CVE-2023-36025 – This is a Security Feature Bypass vulnerability in Windows SmartScreen that can allow an attacker to bypass Windows Defender SmartScreen checks and their associated prompts. This was detected in the wild by Will Metcalf (Splunk), Microsoft Threat Intelligence, and the Microsoft Office Product Group Security Team. Although it is only rated as Important, it has a CVSS score of 8.8 and is known to have been exploited in the wild; users should look to patch this vulnerability as soon as possible to prevent exploitation. The user would have to click on a specially crafted Internet Shortcut (.URL) or a hyperlink pointing to an Internet Shortcut file to be compromised by the attacker.
2. CVE-2023-36033 – This is an EoP vulnerability in the Windows DWM Core Library that can allow an attacker to gain SYSTEM privileges. The vulnerability is considered Important, with a CVSS score of 7.8. Since this is known to have been exploited in the wild, users should look to patch this vulnerability as soon as possible to prevent potential exploitation. An attacker would need local access with low privileges and no user interaction to exploit this vulnerability.
3. CVE-2023-36036 – This is another EoP vulnerability, this time in the in the Windows Cloud Files Mini Filter Driver, that can allow an attacker to gain SYSTEM privileges. Also rated as Important, with a CVSS score of 7.8. Again, since this is known to have been exploited in the wild, users should look to patch this vulnerability as soon as possible to prevent potential exploitation. This attack also requires local access with low privileges and no user interaction to be executed. This issue has been detected and acknowledged by Microsoft Threat Intelligence and the Microsoft Security Response Centre.
Critical
1. CVE-2023-36052 – This is an Information Disclosure vulnerability in Azure CLI REST Command that could allow an unauthenticated attacker to recover plaintext passwords and usernames from log files. Identified as Critical with a CVSS score of 8.6, it presents attackers with a low attack complexity and no prerequisites for user interaction or special privileges. Although exploitation is considered less likely, due to the high severity of potential confidential information exposure, it is recommended that customers using affected CLI commands update their Azure CLI version to 2.53.1 or above to mitigate the risks.
2. CVE-2023-36397 – This is an RCE vulnerability in Windows Pragmatic General Multicast (PGM) that is rated as Critical with a CVSS score of 9.8. It allows an attacker to send a specially crafted file over the network to a system running the Windows message queuing service in a PGM Server environment to execute malicious code. Exploit code maturity is Unproven, and exploitation is currently considered less likely. However, systems with the Windows message queuing service enabled and TCP port 1801 listening are vulnerable.
3. CVE-2023-36400 – This is an EoP vulnerability in Windows HMAC Key Derivation that can allow an attacker, in a low privilege Hyper-V guest environment, to execute code on the Hyper-V host, effectively breaching the guest's security boundary. The vulnerability is rated as Critical with a CVSS score of 8.8. The exploit's code maturity is Unproven, but exploitation is considered less likely at the time of reporting. An attacker would need to log on to the system and run a specially crafted application to exploit this vulnerability and potentially gain SYSTEM privileges.
Adobe
Adobe has released 14 patches this month, addressing 76 vulnerabilities – more than 5x the number of vulnerabilities as last month. The applications in question are:
- ColdFusion – 3 critical and 2 important
- RoboHelp Server – 4 critical and 1 important
- Acrobat and Reader – 9 critical and 1 important
- InDesign – 6 important
- Photoshop – critical and important
- Bridge – no critical or important
- FrameMaker Publishing Server – 1 Critical
- InCopy – 1 critical
- Animate – 1 important
- Dimension – 1 important
- Media Encoder – 4 critical
- Audition – 6 critical and 2 important
- Premiere Pro – 5 critical
- After Effects – 6 critical
All of these vulnerabilities are rated as a priority 3 by Adobe, meaning they relate to a product that has historically not been a target for attackers, although some of these are known to have been targeted previously.
Cisco
Cisco has so far released 35 advisories since last Patch Tuesday, with 3 rated as Critical and 13 as High. The Critical vulnerabilities relate to Cisco Firepower Management Center, Cisco IOS XE (with web UI enabled), and Cisco Catalyst SD-WAN Manager.
Fortinet
Fortinet has released three advisories in November, all with a severity rating of High, and with CVSS scores between 7.1 and 8.1.
- FG-IR-22-299: FortiClient (Windows) - Arbitrary file deletion from unprivileged users
- FG-IR-23-274: FortiClient (Windows) - DLL Hijacking via openssl.cnf
- FG-IR-23-385: curl and libcurl CVE-2023-38545 and CVE-2023-38546 vulnerabilities
SAP
SAP has released 3 new security notes and 3 updates to previous security notes, significantly less than last month. Only two of these CVEs are rated “High” or “Hot News” (Very High), with CVSS scores of 9.8 and 9.6 respectively. The products affected by the high to very high rated CVEs are:
- SAP CommonCryptoLib
- SAP NetWeaver AS ABAP
- SAP NetWeaver AS Java
- ABAP Platform of S/4HANA on-premise
- SAP Web Dispatcher
- SAP Content Server
- SAP HANA Database
- SAP Host Agent
- SAP Extended Application Services and Runtime (XSA)
- SAP SSOEXT
- SAP Business One
VMware
VMware have released a patch for a vulnerability in VMware Cloud Director (VCD) Appliance, affecting version 10.5 if upgraded from 10.4.x or below. This is an authentication bypass vulnerability that could allow an attacker with network access to bypass the login restrictions when authenticating on port 22 or port 5480. This vulnerability is rated as Critical and has a CVSS score of 9.8.
Industrial Control Systems
Any customers utilising industrial control systems (ICS) should be aware of two new security advisories regarding AVEVA and Rockwell Automation.
As always, users are recommended to install the latest security updates when possible to protect their systems from potential threats.

