It’s a good start to the year, with most companies releasing a lower-than-average number of security patches!
Microsoft
In their January Patch Tuesday release, Microsoft has addressed 47 vulnerabilities, with just 2 of those rated as Critical and none being zero-day vulnerabilities. The patches cover a broad array of applications and services, including Windows, Visual Studio, .NET, Office, SharePoint, Azure, and more. Additionally, there have been 4 Edge/Chromium based vulnerabilities identified, as well as one non-Microsoft vulnerability affecting SQLite highlighted.
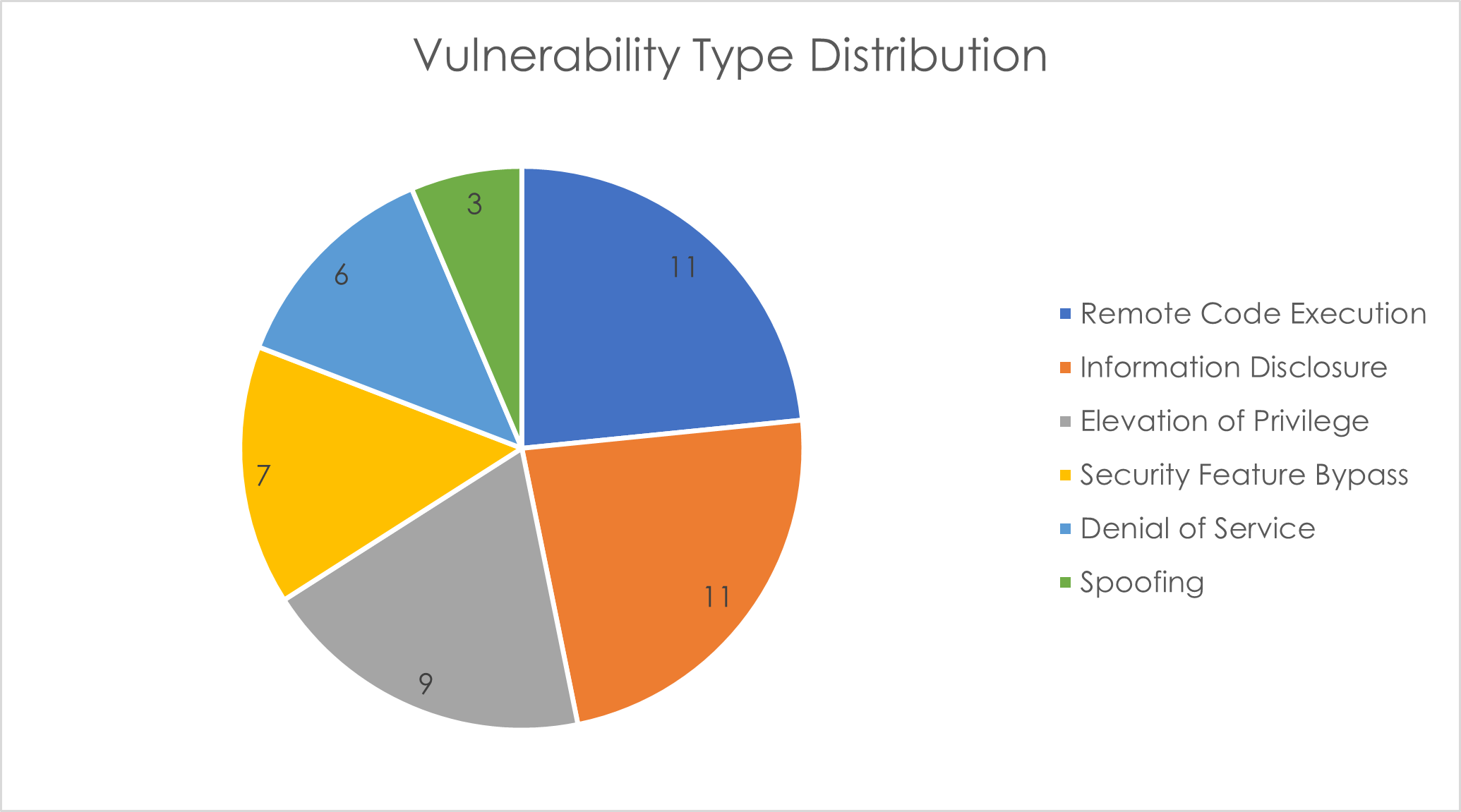
This month's vulnerabilities chiefly revolve around Remote Code Execution (RCE), Information Disclosure, and Elevation of Privilege (EoP). Outlined below are the Critical vulnerabilities detailed in this month’s Patch Tuesday:
1. CVE-2024-20674 – This is a Security Feature Bypass vulnerability in Windows Kerberos that can allow an attacker to impersonate users and bypass authentication features. This vulnerability is ranked as Critical with a CVSS score of 9.0. Successful exploitation is noted to be “More Likely” due to the low attack complexity, low privileges required, and no user interaction; although the attacker must first gain access to the restricted network. An attacker could exploit this vulnerability by conducting a machine-in-the-middle (MITM) attack or other local network spoofing techniques and sending a malicious Kerberos message to spoof themselves as the Kerberos authentication server.
2. CVE-2024-20700 – This is a Remote Code Execution vulnerability in Windows Hyper-V that can allow an attacker to execute arbitrary code on the host system. It has been rated as Critical and a CVSS score of 7.5, although exploitation is noted to be “Less Likely”. The attack complexity is considered high, and the attack vector is adjacent, indicating that the attacker would need to have access to the restricted network before they can execute the attack. There are no privileges or user interaction required, which increases the potential impact if an attacker can overcome the other complexities.
SQLite
CVE-2022-35737 – This is an array-bounds overflow vulnerability in SQLite, ranging from version 1.0.12 to before 3.39.2, that can occur when billions of bytes are used in a string argument to a C API. As this vulnerability could lead to a potential overflow, it is advisable for developers and users of applications depending on SQLite to ensure they've applied the necessary patches or updates to mitigate any risks associated with this vulnerability.
Adobe
Adobe has released just one patch this month, addressing 6 vulnerabilities. The application in question is Substance 3D Stager. All six of the vulnerabilities are rated as Important, the majority of which result in Memory Leak, with one vulnerability resulting in Arbitrary Code Execution
This patch is rated as Priority 3 by Adobe, meaning it relates to a product that has historically not been a target for attackers; however, users are still recommended to patch this when possible.
Cisco
Cisco has so far released one advisory for just two vulnerabilities in January, both with an impact rating of Medium. The vulnerabilities both affect Cisco Identity Services Engine, and are both forms of Privilege Escalation attack (one local and one remote).
SAP
SAP has released 10 new security notes and 2 updates to previous security notes. Seven of these CVEs are rated “High” or “Hot News” (Very High). The products affected by the high to very high rated CVEs are:
- SAP BTP Security Services Integration Library
- SAP Edge Integration Cell
- SAP Application Interface Framework
- SAP Web Dispatcher
- SAP NetWeaver AS ABAP and ABAP Platform
- SAP GUI connector for Microsoft Edge
- SAP GUI connector for Microsoft Edge
Industrial Control Systems
Any customers utilising industrial control systems (ICS) should be aware of four security advisories regarding:
- Rockwell Automation FactoryTalk Activation
- Mitsubishi Electric Factory Automation Products
- Unitronics Vision and Samba Series (Update A)
- Cambium ePMP 5GHz Force 300-25 Radio (Update A)
As always, users are recommended to install the latest security updates when possible to protect their systems from potential threats.

