In this edition, we will focus on the patches by Microsoft, Adobe, Apple, Atlassian, Cisco, Google, SAP, VMware and WordPress.
Microsoft have addressed just 34 vulnerabilities this month, almost half the number of vulnerabilities as we saw in the previous Patch Tuesday roundup, truly a Christmas miracle! (Although other vendors have not been so kind!)
Microsoft
In their December Patch Tuesday release, Microsoft have addressed just 34 vulnerabilities, with 4 of those rated as Critical and no zero-day attacks affecting Microsoft products. The patches cover a broad array of applications and services, including Windows, Office, Dynamics, Azure, and Defender. Microsoft have also addressed an additional 77 vulnerabilities between the last Patch Tuesday update and today's.
Although there have been no Microsoft product related zero-day vulnerabilities identified, Microsoft have released a patch for an AMD zero-day vulnerability disclosed in August which had previously not been patched (CVE-2023-20588).
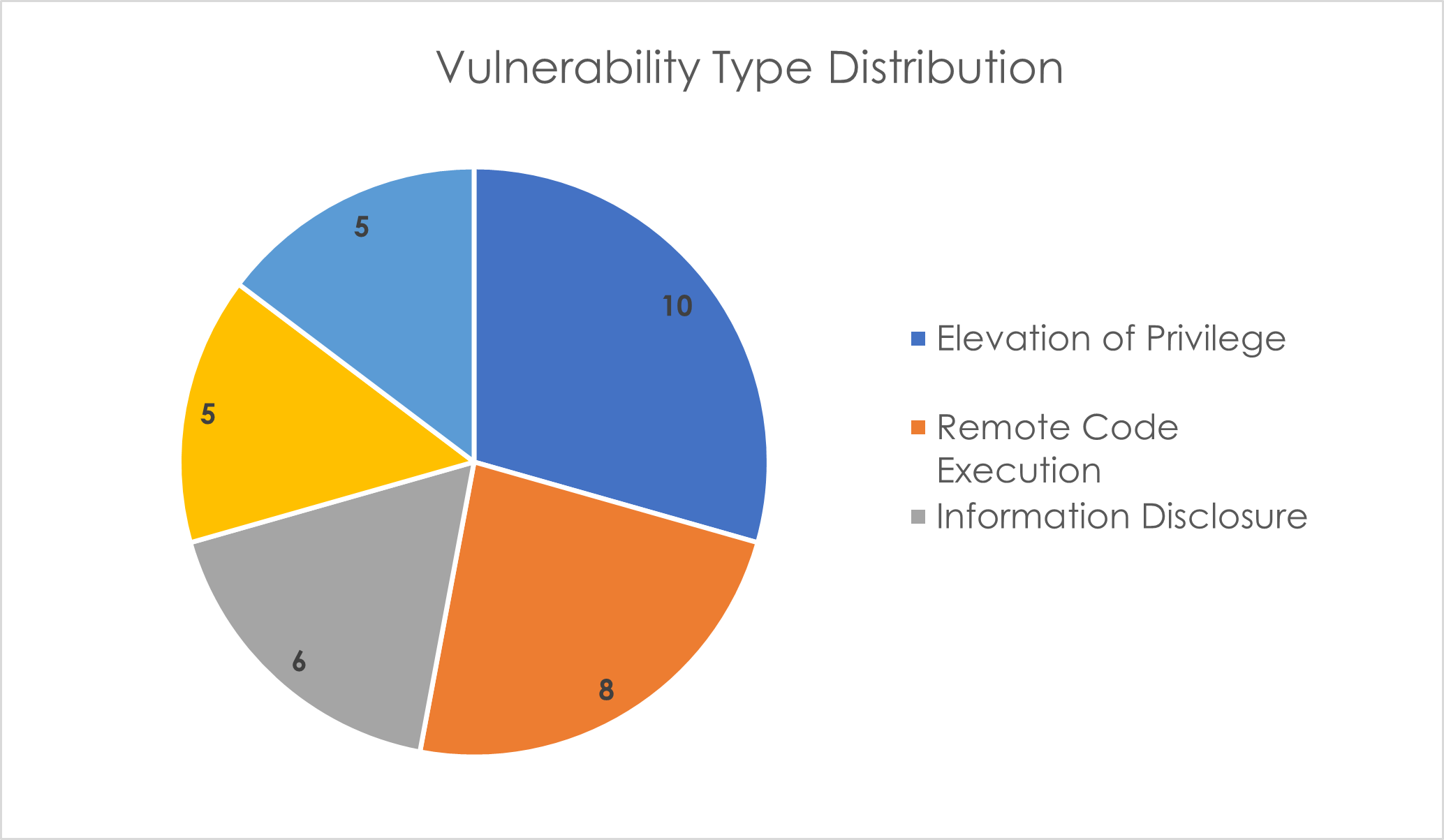
This month's vulnerabilities chiefly revolve around Elevation of Privilege (EoP), Remote Code Execution (RCE), and Information Disclosure. Interestingly there have been no Security Feature Bypass vulnerabilities disclosed this Patch Tuesday.
Outlined below are the critical vulnerabilities detailed in this month’s Patch Tuesday:
Critical
1. CVE-2023-35628 – This is an RCE vulnerability in the Windows MSHTML Platform that can allow an attacker to execute arbitrary code on the victim's machine without any user interaction. This vulnerability is rated as Critical, with a CVSS score of 8.1, and is rated as “Exploitation More Likely”. To exploit this vulnerability, an attacker could send a specially crafted email that triggers automatically when it is processed by the Outlook client, meaning exploitation can occur before the email is even viewed in the Preview Pane. Although rated as “Exploitation More Likely” this is noted to be a very sophisticated attack, relying on complex memory shaping techniques.
2. CVE-2023-36019 – This is a spoofing vulnerability in Microsoft Power Platform Connector that can allow an attacker to trick a user into clicking on a maliciously crafted URL that could then execute scripts in the victim's browser, potentially leading to unauthorised actions. It has a Critical severity rating with a CVSS score of 9.6, although is noted to be “Exploitation Less Likely”. To exploit this vulnerability, an attacker could manipulate a malicious link, application, or file to disguise it as a legitimate link or file to trick the victim. Microsoft has taken mitigation steps by requiring new custom connectors that use OAuth 2.0 for authentication to have a per-connector redirect URI since November 17, 2023, and existing OAuth 2.0 connectors must be updated to use this security measure before February 17th, 2024. Microsoft have notified affected customers through the Microsoft 365 Admin Centre; however custom connectors also need to be validated.
3. CVE-2023-35641 – This is an RCE vulnerability in Microsoft's Internet Connection Sharing (ICS) that can allow an attacker to execute arbitrary code on the affected system without requiring user interaction. The vulnerability is rated as Critical, with a CVSS score of 8.8, and noted to be “Exploitation More Likely”. The attack vector is adjacent, meaning the attacker must be on the same network segment as the victim to exploit the vulnerability. An attacker could exploit this by sending a maliciously crafted DHCP message to a server running the ICS service.
4. CVE-2023-35630 – This is a similar RCE vulnerability in Microsoft's ICS that can allow an attacker to execute arbitrary code on the affected systems, this time by modifying an option->length field in a DHCPV6_MESSAGE_INFORMATION_REQUEST input message. It is categorised as Critical, with a CVSS score of 8.8; however, it is rated as “Exploitation Less Likely”.
All vulnerabilities should be patched when possible, however Critical vulnerabilities should be patched as a priority.
Adobe
Adobe has released nine security updates this month, addressing 73 vulnerabilities – more than five times the number of vulnerabilities as last month. The applications in question are:
Prelude – No Critical or Important vulnerabilities
Illustrator – 3 Critical
InDesign – 2 Important
Dimension – 1 Important
Experience Manager – 47 Important
Substance3D Stager – 2 Important
Substance3D Sampler – 6 Critical
Substance3D After Effects – 3 Critical
Substance3D Designer – 1 Critical and 3 Important
All of these vulnerabilities are rated as a priority 3 by Adobe, meaning they relate to a product that has historically not been a target for attackers.
Apple
Apple has released security updates for almost all of its software, including Safari, iOS and iPadOS, Sonoma, Ventura, and Monterey, to address multiple vulnerabilities.
Atlassian
Atlassian has released four Security Advisories for Critical vulnerabilities in December, as well as an additional seven Security Bulletins for non-critical vulnerabilities. Listed below are the Critical vulnerabilities:
· RCE Vulnerability in Confluence Data Center and Server
· RCE Vulnerability in Atlassian Companion App for MacOS
· RCE Vulnerability in Assets Discovery
· SnakeYAML library RCE Vulnerability impacts Multiple Products
Cisco
Cisco has so far released 3 advisories for 3 vulnerabilities in December, with the impact ratings ranging from Medium to Critical. It is not yet clear which products the Critical Apache Struts Vulnerability affects, with Cisco currently investigating its product line to determine which products may be affected by this vulnerability and the impact on each affected product.
Cisco has just now published a Security Advisory for the HTTP/2 Rapid Reset Attack that was previously outlined in October’s Patch Tuesday roundup. This vulnerability is rated as High, and the list of affected products is long.
Google has released 85 Android Security Updates in December, including a Critical RCE vulnerability that requires no user interaction and no elevated privileges to execute (CVE-2023-40088).
SAP
SAP has released 15 new security notes and 2 updates to previous security notes. Eight of these CVEs are rated “High” or “Hot News” (Very High). The products affected by the high to very high rated CVEs are:
- SAP Business Client
- SAP Business Technology Platform (BTP) Security Services Integration Libraries
- SAP ECC and SAP S/4HANA (IS-OIL)
- SAP Commerce Cloud
- Business Objects BI Platform
- SAP GUI for Windows and SAP GUI for Java
- SAP EMARSYS SDK ANDROID
VMware
VMware has released a patch for a vulnerability in the VMware Workspace ONE Launcher, affecting just Android. This is an Elevation of Privilege attack in which a malicious actor with physical access to Workspace ONE Launcher could utilise the Edge Panel feature to bypass setup to gain access to sensitive information. This vulnerability is rated as Moderate and has a CVSS score of 6.3.
WordPress
WordPress has released a patched version (6.4.2) that addresses an RCE vulnerability that has the potential to allow arbitrary PHP code execution. Although most updates are automatic, all users utilising WordPress should manually check if the update has completed. This is especially important, as almost half of all sites on the internet utilise WordPress.
Industrial Control Systems
Any customers utilising industrial control systems (ICS) should be aware of seven security advisories regarding:
- Schneider Electric Easy UPS Online Monitoring Software
- Mitsubishi Electric MELSEC iQ-R, iQ-L Series and MELIPC Series (Update B)
- Mitsubishi Electric FA Engineering Software Products
- Schweitzer Engineering Laboratories SEL-411L
- Johnson Controls Metasys and Facility Explorer
- Sierra Wireless AirLink with ALEOS firmware

