In this blog we will cover how to set yourself up for success in building security operations capabilities, select technology, mature existing practises and how to integrate the SOC into the broader organisation.
1. Build capabilities first
According to Aristotle, “The whole is greater than the sum of its parts”. Now I’m no 5th century philosopher, but this quote resonates with me when applying it to security operations. Too often, we come across Security Operation Centres that have been built on someone’s love of a technology, or another person’s desperation to satisfy a compliance mandate. But as George Eliot (or Mary Ann Evans without the pseudonym) would say, “it’s never too late to be what you might have been.”
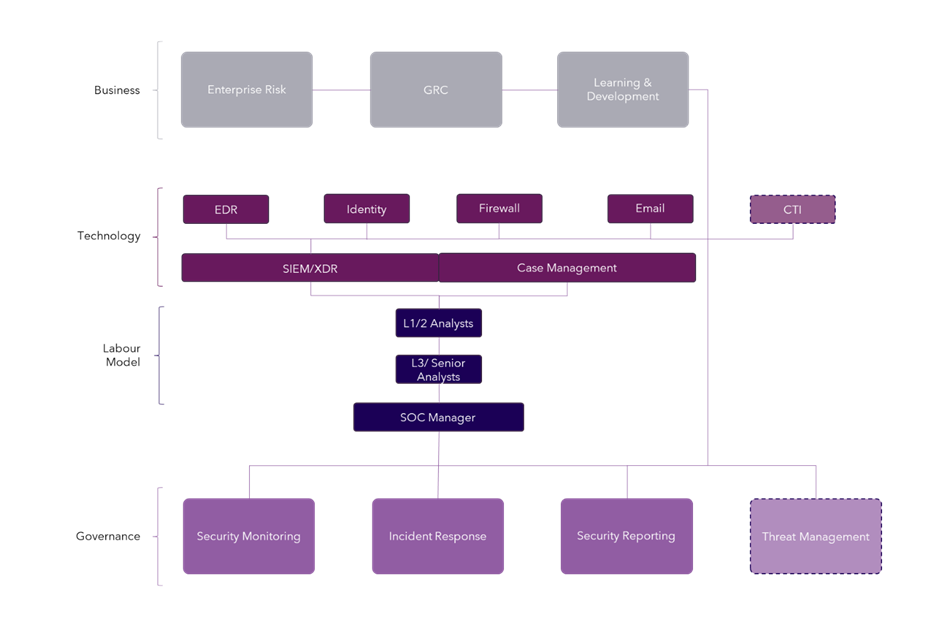
We must start with the capabilities we want our SOC to provide to the rest of the organisation. A great way of viewing this is by thinking in ITIL (Information Technology Infrastructure Library) terms and creating a SOC service catalogue. Arguably, I would say it starts with the below:
- Security monitoring governs the information we need to garner from our environments within Information Technology. Ideally, we should set a minimum standard for the types of data, or data schemas that we need, to provide high-fidelity information for our SOC Analysts to act upon. So, for example, we know we need to capture file modification logs and process trees to effectively detect potentially malicious techniques a threat actor may use on our endpoints. This would lead us to the technology or log source that we need to collect information from, in this case, most likely an Endpoint Detection Response (EDR) tool.
- Incident response is our bread and butter, the fundamental work we conduct within the SOC. An incident response is not the hair-raising moment we encounter ransomware, but the routine processes we use to conduct investigations into potential incidents on a daily basis. This is commonly where we create ‘playbooks’; processes that govern exactly how we respond to incidents of a certain type.
- Reporting may seem like the odd one out, but it is one of the most important things to come out of the SOC, as opposed to come into the SOC in the guise of information. We must inform everyone in the business, from Cyber and IT leadership, up to board level, what we are seeing and doing within the four walls of our SOC. This service catalogue should define types of reports, standard metrics, audiences and frequency of the reports.
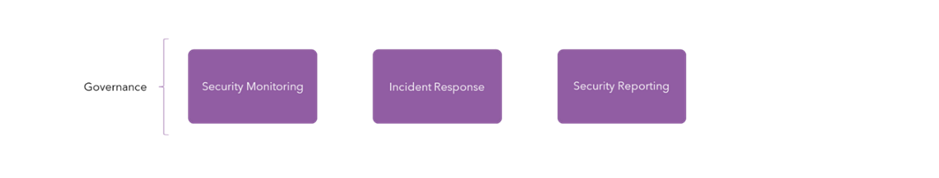
It is important to note that all services catalogues, like their ITIL equivalents, should contain processes you follow and the aligned persons that are Responsible, Accountable, Consulted and Informed with all relevant stakeholders in agreement.
2. Show your organisation what you’re doing
Reporting is just one part of the story. The SOC should have an identity just like your service desk, regardless of whether it is largely outsourced or mainly insourced. Centres of Excellence (or CoEs) is an all-too-common phrase we see now, but your SOC doesn’t have to go that far. Consider getting regular representation from the SOC present at senior leadership meetings, presenting incident response metrics, updating on resource, team structure and being the centre of regular business communication. This is the same team we rely on to keep our organisation safe from cyber threats, as we do to send us test phishing messages and help us with cyber awareness training.
Organisationally, presenting how the SOC operated to IT leadership in the form of a service library impresses the importance of it as an operational component within the business. This is also where you can build in your labour model. How are we staffing the SOC? Do we have 24/7/365 response coverage? Both questions can be answered with outsourced and insourced labour models.
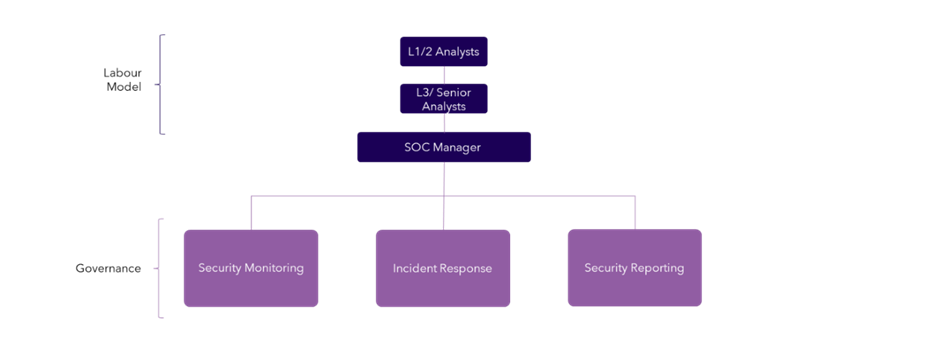
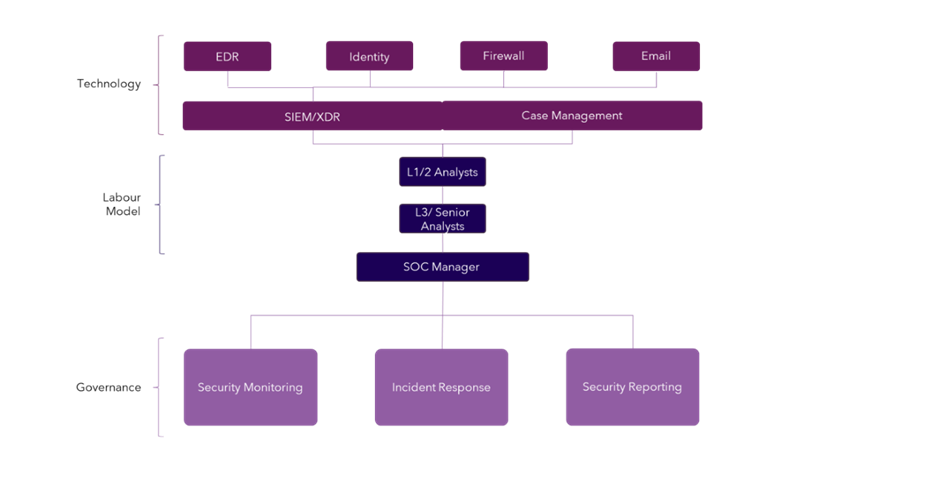
3. Select technologies that support your defined capabilities
There are dozens of technologies we can implement within the SOC, but not all of them will improve existing, or help us develop new capabilities in a clear way. The underpinning technology most people go to when thinking of security operations is a logging and monitoring tool, such as a Security Information Event Management (SIEM) or an Extended Detection Response product (XDR). These systems are simple. Essentially they are data collection technologies that consume different types of event data in both structured and raw formats. They then store and parse this data in a referenceable format. These types of technology usually have analytic engines layered on top - whether it be a machine learning (ML) algorithm or a search-based piece of logic like a query language - to enable our security analysts to draw conclusions from a security context.
The same outcome can be achieved with both SIEM and XDR, but in slightly different ways, priced in alternating fashion. Many are starting to compare a SIEM to a private security data lake, where data ingest is purposeful and use cases are derived directly from the data you want to satisfy them. XDR on the other hand is being compared to a public data lake, where you send data from everything you have that it can parse. The XDR solution then derives what it thinks is the value you need. Both tools help you satisfy the goal that you need your analysts to achieve – make decisions.
A case management tool is also critical. This is where a record of all your security incidents will reside, along with the capabilities to assign relevant incidents a priority and severity level, and get it to the team it needs, for activities like containment. The by-product of this, is that it will most likely form the basis of the data you need for your important reporting service catalogue.
Ancillary technologies then often fall into two categories:
- Those that provide additional insight – think new security controls such as a Cloud Security Posture Management (CSPM) tool that may now give more accurate prioritisation levels to cloud assets.
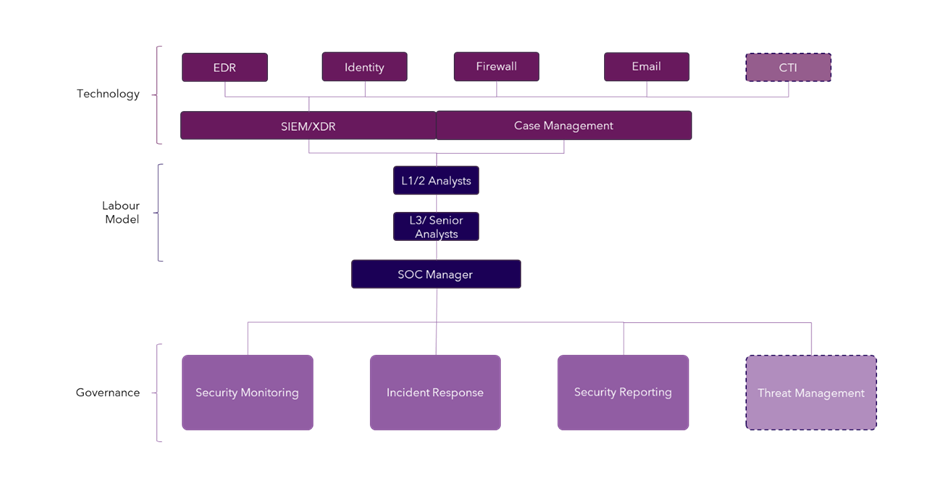
- Those that provide new capabilities – this is where there could be arguments, but two good examples are a Vulnerability Management Scanner (if not implemented already) or a Cyber Threat Intelligence (CTI) platform which in it’s very basic guise can provide additional insight via things like Indicators of Compromise (IoC) or provide the basis of an entire new capability like Threat Management.
4. Never stop improving
One thing we can all agree on, is that cyber security is fast paced, and we are different to other operations teams throughout the business. Adversaries are continuously trialling new techniques and procedures, weaponising new malware, and being more courageous with their attempts against people. Therefore, the SOC must continue to evolve by improving on existing and adding new capabilities. This can be done via the classic people, process and technology triad.
- People – upskill and hire. This can be done in reaction to a shift in technology, threats or in direct response to developing new capabilities like Threat Management. It can also be in response to integration of new technologies that enhance your core capabilities like Security Orchestration Automation Response (SOAR) platforms, whereby you may not need a Level-1 analyst anymore due to automatic enrichment, meaning you can upskill them.
- Process – improve and automate. Like the example above, SOAR features can enhance existing processes by making them optimal, reducing human interaction, decreasing key metrics like Mean-Time-To-Respond (MTTR) and freeing up time for more proactive activities. Or it could be the introduction of a new process for a new capability like threat hunting and introducing a framework such as Targeted Hunting integrating Threat Intelligence (TaHiTI).
- Technology – support new capabilities with new tools. Sometimes, the proper introduction of technology can boost existing capabilities and form a great basis to add new ones. A great example of this is a Cyber Threat Intelligence (CTI) platform. This can enrich current capabilities like incident response and vulnerability management, but also form the basis for more proactive capabilities like Threat Management and Hunting.
5. Give the SOC a platform
“All that is gold does not glitter.” – an apt quote from J.R.R Tolkien’s The Fellowship of The Ring, where we can also compare what you’ve now built to Sauron’s all-seeing eye. But it is true, we must now elevate the SOC so that it is the glittering jewel in your security crown.
Now that you have solid capabilities, an accurate labour model, a great toolset, and earmarked areas for advancement – we can integrate the SOC into a broader selection of business units.
- Merger and Acquisition: threat Management and research can bring invaluable information to your commercial teams when looking at acquiring another businesses, impact their valuation, and inform your risk team of anything to be aware of when integrating into your broader IT estate.
- Governance, Risk and Compliance (GRC): this one is essential when your SOC is operational. GRC is how we lead and influence cyber security strategy at the highest level. The SOC obviously helps us comply with external influences like Contractual, Statuary and Regulatory compliance, but it can also provide vital information for internal assurance, investigations and help us pursue new certification for contractual obligations.
- Internal awareness training: we all have commitments to mandatory yearly training, but what about additional training to bolster knowledge and reduce the risk of insider threat? This is an ideal opportunity to engage the best and brightest from the SOC to the entire organisation, delivering friendly threat updates, in-person phishing training and physical security.
These five steps form the basis of advice we give to our customers on security operations, and we hope you’ve taken some insights from them. For any queries relating to SOC please reach out to your Softcat account manager or our Sales team about our security consultancy services, managed cyber services and assessment services.

